
Antenna Rotor - Part 1
A few years ago I bought a Pelco Câmera Rotor, model PT175-24P. This rotor is made for carrying a camera with up to 8kg, and contains two biphase reversable motors internally. My idea was (and is) to put a satellite dish coupled, and control its movement to track satellites. Then I could use it to receive Low Orbit Satellites. Internal Schematics The problem of the original system from pelco, is that they’re two 24V AC Motors, which would require a VFD (Variable Frequency Driver) to control the speed and a closed-loop system with a angle sensor. That would make it...
Introduction to FPGA

(So far) Only available in Portuguese
Hacking a ESP32 into FPGA Board
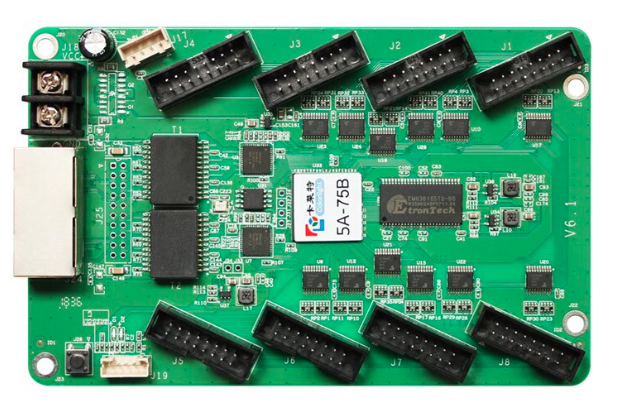
Hacking a ESP32 into FPGA Board Colorlight Hub 5A-75B V6.1 Board Last year I saw a russian guy that found out that this cheap board (US$15~) had an Lattice ECP5 FPGA, which is compatible with Open Source Tool-chains for synthesis. He was running a RISC-V Core inside that and piping the serial through the ethernet ports. I wanted to get one and start playing by myself. These boards are relatively cheap, about US$15 and contains a Lattice ECP5 FPGA ( LFE5U-25F-6BG381C ), 4MB DRAM, Two Gigabit Ethernet and several level shifters for I/O. This is good because: That’s a very...
Hack a Sat - Talk to me, Goose
Hack a Sat — Talk to me, Goose The “Talk to me, Goose challenge” on Hackasat This challenge is just after the “Can you hear me now?” challenge (see Hack a Sat - Can you hear me now? ). Now LaunchDotCom has a new Satellite called Carnac 2.0. There are two attached files. The first one is the manual of the satellite in which we can see the onboard equipment: System Diagram of Carnac 2.0 Satellite There is also a XTCE file in which the Telemetry Data looks the same as previous challenge, but now there is a Command Section which implies...
Hack a Sat - Phasors to Stun
Hack a sat — Phasors to Stun The challenge I got really excited about it because its a SDR one. And everyone that knows me know that I love SDR stuff. The zip file itself contains a wav file which they told us is not an audio but an radio signal File command to show what the wave file is If we open in audacity we will se a very interesting pattern: Audacity view of the wave file That looks like a 2-FSK demodulated file (see https://en.wikipedia.org/wiki/Frequency-shift_keying). When you demodulate a 2-FSK I/Q from correctly from a Radio, it will...